Hancitor continues to exploit fake DocuSign emails to lure new victims. Researchers from Cofense have discovered yet another campaign distributing it, and apparently, that’s not the only one. As we have previously discussed, Hancitor (AKA CHanitor, Tordal) is a popular macro-based malware dropper, distributed via malicious Office documents, that is particularly hard to detect, not only because it is distributed via a Google Docs link, but also because it has multiple mechanisms to detect if it can run in the infected endpoint (for example, it checks if it has been run before in the same endpoint). Hancitor has been seen distributing multiple payloads, including FickerStealer or Cobalt Strike.
In this latest campaign, the victim receives a fake DocuSign email delivering an invoice (yes, money is always a good reason to open a malicious link). DocuSign templates are quite a common pattern for Hancitor. In particular, the link inside the email points to a Google Docs template that prompts the user to download a malicious .DOCX file. Once executed the malicious document downloads the payload.
As we have previously pointed out, the technique of exploiting a legitimate cloud service for redirection is not new and has been used in recent campaigns with Box, Sharepoint, Google Drive, and Dropbox to deliver malware or serve phishing pages.
How Netskope mitigates this threat
There are multiple stages of the attack chain where the Netskope Next Gen SWG can mitigate this threat.
- It is possible to block the access (and, in general, enforce granular controls) to dozens of non-corporate cloud storage services (including personal instances of corporate services or non-corporate instances abused by the attackers).
- The second redirection can be prevented by the content filtering engine that offers 16 granular security risk categories including phishing and malware distribution.
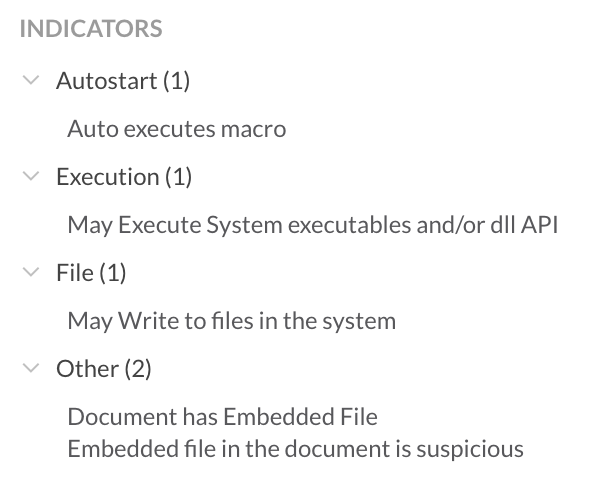
The download of a malicious document can be prevented by the Advanced Threat Protection Engine that provides an ML-based Office Scanner for malicious documents. In particular, the Office Scanner detects Hancitor documents as “Gen.Malware.Detect.By.StHeur.MsOffice” detecting the following indicators of malicious behavior:




 Back
Back 





















 Read the blog
Read the blog